Server Side Encryption
There are two types of server side encryption that can be set in Amazon s3 - AES256 or AWS:KMS.
AES256 setup instructions
Option 1 - To set AES256 as your default Server Side Encryption, simply define it as your algorithm in your call to PUT /encryption:
{ "encryptionAlgorithm": "AES256" }
Note:
Option 2 - AES256 encryption can be set per data resource. This can be done by setting "x-amz-server-side-encryption" and "x-amz-server-side-encryption-customer-key" in the header of your request. The key is an arbitrary, user-specified string.
"x-amz-server-side-encryption": "AES256" "x-amz-server-side-encryption-customer-key": "xxxxxxxxxxxxxxxxxxxxxxxx"
Note:
x-amz-server-side-encryption-customer-key
AWS:KMS setup instructions
Option 1 - To set AWS:KMS as your default Server Side Encryption, set the type of algorithm and your AWS key in your call to PUT /encryption:
{ "encryptionAlgorithm": "aws:kms", "kmsKey": "xxxxxxxxxxxxxxxxxxxxxxxx" }
Option 2 - Similar to option 1, you can set the default encryption without generating a new key. AWS will retrieve the default key configured in your s3 policy via IAM. Call PUT /encryption and pass just the algorithm:
{
"encryptionAlgorithm": "aws:kms"
} Option 3 - AWS:KMS can be set on the data resource level. To do this, pass "x-amz-server-side-encryption" and "x-amz-server-side-encryption-aws-kms-key-id" in the header of your request.
" x-amz-server-side-encryption": "aws:kms" "x-amz-server-side-encryption-aws-kms-key-id": "xxxxxxxxxxxxxxxxxxxxxxxx"
Note:
Client Side Encryption
The Amazon S3 connector now also supports client side encryption. Follow the steps provided in Amazon S3 Documentation to learn how to use a master key stored within your application to enable client side encryption.
To enable client side encryption on the UI:
- The Enable Client Side Encryption
field or in config
clientside.encryption.enabledshould be set to true. - The Client Side Encryption Key or in config
clientside.encryption.keyshould be of lengths of 16 or 24 or 32 characters.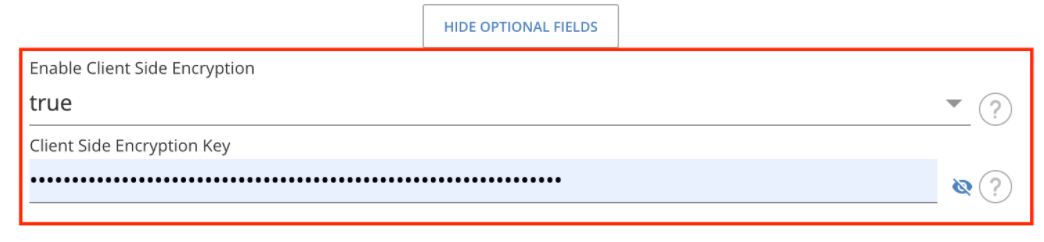
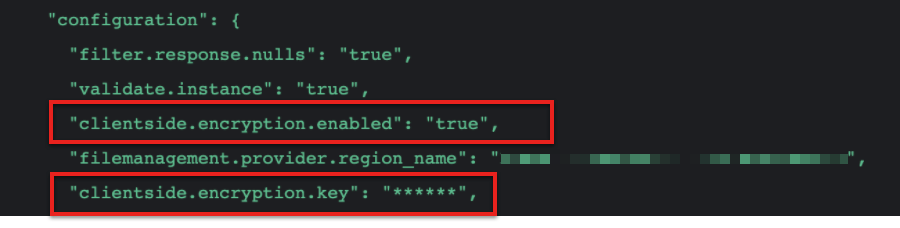
clientside.encryption.enabled and clientside.encryption.key are mandatory to enable client side encryption. To disable it, pass clientside.encryption.enabled: false.

